Vibe-Coded Malware in VS Code Marketplace: Why Developer Tools Are Now Front-Line Threats
A malicious VS Code extension dubbed “vibe-coded” slipped into the official marketplace and launched ransomware-style attacks on developer machines. Discover how this supply-chain threat works, what Indian developers must watch out for, and how to protect your coding environment.
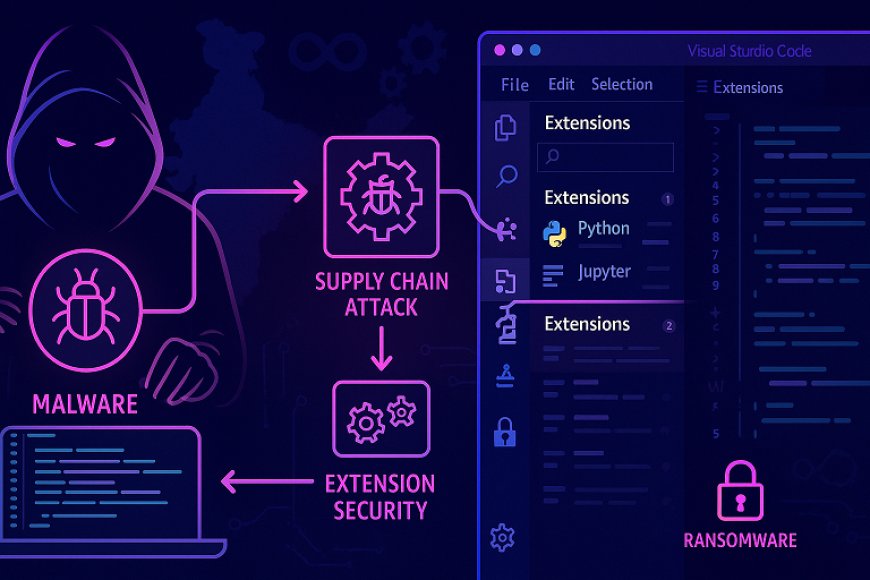
In a startling escalation of developer-tool threats, cybersecurity researchers have uncovered a malicious Visual Studio Code extension dubbed “vibe-coded” that entered the official Visual Studio Code Marketplace with embedded ransomware-style capabilities. The extension, published under the alias “susvsex” by “suspublisher18”, was engineered to automatically zip, upload, and encrypt targeted project directories immediately upon activation — signaling a major breach in the developer-ecosystem supply chain.
How the Vibe-Coded Attack Worked
- Disguised as a normal extension: The extension appeared as a harmless “UI helper” and included vague documentation that masked its true purpose.
- Activation event trigger: Once installed, it activated through a post-install script named
zipUploadAndEncrypt(), compressing local files and sending them to an attacker-controlled endpoint. - Malicious payload delivery: Hidden obfuscated JavaScript downloaded a secondary payload that attempted to execute ransomware-like encryption routines.
- Marketplace bypass: Despite including strings like “zip” and “encrypt” in its description, the extension passed Microsoft’s automated checks and remained live for several hours before removal.
Why This Attack Marks a Shift in Developer-Tool Threats
Unlike typical end-user malware, the “vibe-coded malware VS Code marketplace” incident targets developers directly — weaponizing trusted ecosystem components. This represents a new phase of software supply-chain attacks focused on code creators instead of consumers.
- Compromised trust model: When an official extension marketplace is breached, even verified developers face exposure.
- Supply-chain potential: A single update could spread malicious code to thousands of users across enterprises.
- AI-generated code misuse: Indicators suggest that parts of the extension were written by AI, demonstrating how “vibe-coding” — the careless use of AI-generated code — can be exploited for malicious ends.
Impact on Developers and Organizations
The implications reach beyond individual developers — entire teams and companies using synced workspaces may have unknowingly propagated the malicious extension across environments.
- Data theft: The malware attempted to capture environment variables, API keys, and GitHub credentials.
- CI/CD exposure: Build pipelines using infected machines risked secret leaks through cached authentication tokens.
- Corporate vulnerability: Infected endpoints could have triggered downstream attacks via internal repositories or production servers.
India-Specific Risks and Responses
- High developer concentration: India’s massive VS Code user base makes it one of the most affected regions in potential exposure volume.
- Regional extension cloning: Localized forks of the malicious code have already been spotted on GitHub, raising the need for active monitoring.
- Awareness and training: Developer communities should conduct secure-extension audits and educate teams about supply-chain security hygiene.
Hardening Your VS Code Environment — A Quick Checklist
- Verify publisher authenticity: Install only from verified publishers with visible track records and legitimate source repositories.
- Inspect extension code: Review any linked GitHub repository for suspicious calls like
fetch()or file-system access. - Run audits: Use
code --list-extensionsto review all installed extensions and uninstall any unknown packages. - Enable real-time scanning: Keep Microsoft Defender or equivalent security tools active in developer environments.
- Adopt least-privilege principles: Limit extensions’ access to network or file-system APIs wherever possible.
“Developer tools have become the new attack surface. When an IDE extension can quietly encrypt code or steal credentials, the software supply chain itself is under siege.”
Detecting and Cleaning Infections
Developers can quickly detect malicious VS Code extensions by checking for unexpected behavior, such as abnormal network requests or encrypted local files. Use this process to clean your setup:
- Run
code --list-extensionsand identify suspicious entries like vibe-coded or susvsex. - Uninstall using
code --uninstall-extension. - Remove cached files in
%USERPROFILE%/.vscode/extensions(Windows) or~/.vscode/extensions(macOS/Linux). - Perform a full system scan using reputable antivirus tools.
- Rotate all compromised credentials and tokens used within the environment.
FAQs — Understanding the Vibe-Coded Malware Threat
A: A malicious extension uploaded to the VS Code Marketplace that compressed, encrypted, and exfiltrated project files.
Q: How did it get approved on the Marketplace?
A: It bypassed automatic scanning through obfuscation and minimal metadata, masquerading as a harmless testing extension.
Q: What does “vibe-coded” mean?
A: It’s slang for poorly reviewed, often AI-generated code published with minimal oversight — a rising risk in today’s development ecosystem.
Q: Has Microsoft removed it?
A: Yes, the publisher was suspended and related packages were deleted within 24 hours of verification.
Q: How can I stay safe from similar attacks?
A: Verify publisher IDs, use local network monitoring, and audit extension manifests regularly.
Further Reading & References
- The Hacker News – Vibe-Coded Malicious VS Code Extension Found with Built-In Ransomware Capabilities
- CSO Online – Vibe-Coded Ransomware PoC on Microsoft Marketplace
- Bleeping Computer – AI Slop Ransomware Test Sneaks into Marketplace
Sneak peek: The “vibe-coded malware VS Code marketplace” saga is a cautionary tale for every developer. In a world where AI-generated code and rapid publishing collide, the very tools meant to boost productivity can turn into silent attack vectors. Security must now be part of every developer’s workflow.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0














































